Recently I saw an interesting
rtl-sdr article with a
YouTube video on setting up a used Cicso LinkSys EA3500 router with OpenWrt and the RTL-SDR, (the second part of the video is
here).
 |
| Cisco EA3500 with NooElec RTL-SDR |
The video was so interesting, that I found a used EA3500 for sale on
ebay and immediately purchased it to try this myself! (not a single one of my routers has a USB interface. Go figure) There are also used ones on
amazon as well.
Although it was the topic of SDR caught my attention, it is still a pretty good video on OpenWrt.
The cool thing is that when done - I can move my RTL-SDR device anywhere within range of WiFi! Sweet. No longer limited to USB cable distance of my computer.
For stock firmware, there's no username; default password is
admin
You should note that when the router first boots with stock firmware and factory reset, there's NO security on WiFi.
I did this on Windows 10, with the Ubuntu WSL for ssh access and other unix tools like iperf.
My wired test network is setup specifically to allow new devices with the default 192.168.1.1 address to work without having to unplug and re-plug my computer for many devices. However for this exercise I need to connect to OpenWrt before it is configured. So my setup is a little different than the video:
[internet] -- [switch: 192.168.1.x ] --- [yellow ES3500 Internet port]
[blue ES3500 Ethernet port ] --- [my computer]
While videos are cool, they make for poor reference material for later use. It is difficult to "scroll" though a video looking for a particular technical item. I'll keep track of all the details here.
The first reference is to the
WikiDevi Linksys EA3500 page, with a link to the
OpenWrt page for the Linksys EA3500. Despite the name
factory.bin - this is NOT the stock Linksys software. This is the file to download for OpenWrt. There's more information on the
Techdata: Linksys3500 page. That's where you can find a link to
Firmware OpenWrt Install URL.
The first thing I did was brick my router. :( I loaded that openwrt-kirkwood-linksys-audi-squashfs-factory.bin mentioned above. It did not go well. Fortunately there's a
magic sequence of events to restore it. Thanks
mikemccartney for posting these instructions that worked for me:
1 Plug in the EA3500/4500
2 Power led will blink rapidly
3 Power led will turn off
4 As soon as the power led turns off, unplug the router
5 Wait a few seconds
6 Plug the router back in and repeat the above process
Do that three times, on the fourth time keep the router plugged in and let it boot, hopefully you will now have a functioning router again.
I'm just glad I didn't have to figure out how to JTAG the firmware onto the router.
This time when loading
openwrt-kirkwood-linksys-audi-squashfs-factory.bin things went much better.
So back to the video instructions: there's no default web UI when OpenWrt first boots. To initially access the new firmware, use: ssh root@192.168.1.1 and it should look something like this:
0 $ ssh root@192.168.1.1
The authenticity of host '192.168.1.1 (192.168.1.1)' can't be established.
RSA key fingerprint is 6e:6d:a4:4e:83:9e:54:10:b3:be:c0:76:bf:eb:aa:e3.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.1.1' (RSA) to the list of known hosts.
BusyBox v1.24.2 () built-in shell (ash)
_______ ________ __
| |.-----.-----.-----.| | | |.----.| |_
| - || _ | -__| || | | || _|| _|
|_______|| __|_____|__|__||________||__| |____|
|__| W I R E L E S S F R E E D O M
-----------------------------------------------------
DESIGNATED DRIVER (Bleeding Edge, 50107)
-----------------------------------------------------
* 2 oz. Orange Juice Combine all juices in a
* 2 oz. Pineapple Juice tall glass filled with
* 2 oz. Grapefruit Juice ice, stir well.
* 2 oz. Cranberry Juice
-----------------------------------------------------
root@OpenWrt:~#
Next set password with
passwd
command:
root@OpenWrt:~# passwd
Changing password for root
New password:
Retype password:
Password for root changed by root
If you are familar with VI/VIM you can skip this step, otherwise you can install nano:
opkg update
You may wish to save you original configs:
cp /etc/config/network /etc/config/network.bak
cp /etc/config/wireless /etc/config/wireless.bak
Edit /etc/config/network that originally looks like this:
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdbc:cc57:906d::/48'
config interface 'lan'
option type 'bridge'
option ifname 'eth0'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'wan'
option ifname 'eth1'
option proto 'dhcp'
config interface 'wan6'
option ifname 'eth1'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '0 1 2 3 5'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '4 6'
He edits the network from 192.168.1.1 to 192.168.2.1
config interface 'lan'
option ipaddr '192.168.2.1'
and changes the wan interface from
eth1 to
wlan0 for both.
config interface 'wan'
option ifname 'wlan0'
config interface 'wan6'
option ifname 'wlan0'
Then edit /etc/config/wireless that for a default config, that originally looks like this.
config wifi-device radio0
option type mac80211
option channel 11
option hwmode 11g
option path 'mbus/mbus:pcie-controller/pci0000:00/0000:00:01.0/0000:01:00.0'
option htmode HT20
# REMOVE THIS LINE TO ENABLE WIFI:
option disabled 1
config wifi-iface
option device radio0
option network lan
option mode ap
option ssid OpenWrt
option encryption none
config wifi-device radio1
option type mac80211
option channel 36
option hwmode 11a
option path 'mbus/mbus:pcie-controller/pci0000:00/0000:00:02.0/0000:02:00.0'
option htmode HT20
# REMOVE THIS LINE TO ENABLE WIFI:
option disabled 1
config wifi-iface
option device radio1
option network lan
option mode ap
option ssid OpenWrt
option encryption none
Remove the channel selection and enable wifi (by setting disabled to false):
config wifi-device radio0
# option channel 11
option disabled 0
And edit the wifi-iface section for 2GHz:
config wifi-iface
option device radio0
option network wan
option mode sta
option ssid yourssid
option encryption psk2
option key yourwifipassword
Edit the wifi-iface section for 5GHz in a similar manner if you have one (I do not).
The reboot, wait, and ssh to the NEW IP address:
reboot;exit
# wait...
ssh root@192.168.2.1
Once everything is configured, the cable between the yellow Ethernet port and the switch can be removed, as the router is now a station
[internet] -- [WiFi (same as above switched network)]
[WiFi] ---- [blue ES3500 Ethernet port ] --- [my computer]
Other things installed in the video include installing
LuCI (the graphical web gui). Note the video installed regular luci; I prefer the luci-ssl, even though the browser will complain that it is not a secure connection (no trusted root for self-signed cert)
opkg update
# opkg install luci # the non-ssl version
opkg install luci-ssl
/etc/init.d/uhttpd start
/etc/init.d/uhttpd enable
Then see which RTL packages are available:
opkg list | grep rtl
He then goes on to install rtl-sdr
opkg install rtl-sdr
which rtl_fm
which rtl_tcp
rtl_tcp -h
Plugging in my
NooElec RTL-SDR that I received for Christmas (what a cool gift!!) I see this latest entry with
dmesg:
[ 2819.934581] usb 1-1: new high-speed USB device number 2 using orion-ehci
Then simply run rtl_tcp:
root@OpenWrt:~# rtl_tcp
Found 1 device(s):
0: Realtek, RTL2838UHIDIR, SN: 00000001
Using device 0: Generic RTL2832U OEM
Found Rafael Micro R820T tuner
[R82XX] PLL not locked!
Tuned to 100000000 Hz.
listening...
Use the device argument 'rtl_tcp=127.0.0.1:1234' in OsmoSDR (gr-osmosdr) source
to receive samples in GRC and control rtl_tcp parameters (frequency, gain, ...).
Other things installs in the video:
opkg list | grep dump
opkg install dump1090
opkg install iperf
Part two of the video starts out a bit confusing... but skip the first 7 minutes and pick up at the OpenWrt login prompt.
There's a reminder on restarting WiFi:
wifi down; wifi up
# or
ifconfig wlan0 down
ifconfig wlan0 up
Basically to ensure there's an IP address listed for wlan0. (the client DHCP address for your WiFi network; remember this device was configured as STA, not AP (above).
As such, the ES3500 is connected to the "internet" via WiFi instead of via the yellow RJ-45 connector. Thus for wireless access, port forwarding is needed. At first, I setup a simple traffic rule that worked:
However I wanted to follow along and use port forwarding instead, like this:
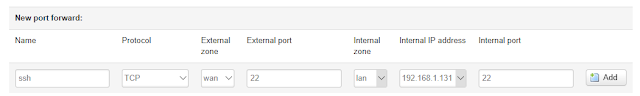 |
| A port forward that looks like it should work, but does not. |
Unfortunately, the video already had many of the port forwards already configured. I had a difficult time with getting ssh working. I kept getting these odd connection refused errors:
gojimmypi@ElectronicsDesk : ~
255 $ ssh root@192.168.1.131
ssh: connect to host 192.168.1.131 port 22: Connection refused
Now "connection refused" is an interesting error. It says things are working but being rejected. I was sure I had it configured correctly. As it turns out there's a feature specifically to allow ssh under System - Administration:
Even setting the "allow remote hosts", I continued to get the port refusal error. So in the video, he connects to the client STA address of the EA3500. Yet when on the local 192.168.2.x network, I was ssh'ing into the router IP address: 192.168.2.1 and not its client STA address of 192.168.1.131 - so I used that as a port forward instead. Note that it shows up in the drop-down as "(Openwrt,lan)" next to the IP addy
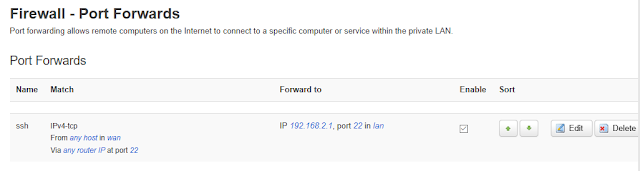
And so once that is working, several other ports also need to be forwarded:
Note that when moving your client computer between the ES3500 network (192.168.2.x) and the local wired/wireless network (192.168.1.x) - there's a delay of up to several minutes in Windows obtaining the new address and getting everything setup, during which you'll see messages like this when attempting ssh:
ssh: connect to host 192.168.1.131 port 22: Software caused connection abort
ssh: connect to host 192.168.1.131 port 22: Resource temporarily unavailable
ssh: connect to host 192.168.1.131 port 22: Network is unreachable
If you still have problems connecting, recheck settings and try reboot. But be patient, it does take some time. Again, note that I believe the port forwards in the video are completely wrong - and the only reason he was able to get it working was the traffic rules. I have no traffic rules - just the port forwards, but to a different address. But then again, I spent the better part of the afternoon playing with this - and the video author sped though the entire process in an impressive 37 minutes apparently with no editing / interruptions. Impressive.
Once that is working, I setup iperf as a server on the EA3500:
iperf -s
In a separate shell, staying local the PC (I also needed to install iperf):
sudo apt-get install iperf
iperf -c 192.168.1.131 -i 3 -t 30
and saw mediocre performance from this "gigabit" router:
------------------------------------------------------------
Client connecting to 192.168.1.131, TCP port 5001
TCP window size: 512 KByte (default)
------------------------------------------------------------
[ 3] local 192.168.1.143 port 5607 connected with 192.168.1.131 port 5001
[ ID] Interval Transfer Bandwidth
[ 3] 0.0- 3.0 sec 6.75 MBytes 18.9 Mbits/sec
[ 3] 3.0- 6.0 sec 8.00 MBytes 22.4 Mbits/sec
[ 3] 6.0- 9.0 sec 7.12 MBytes 19.9 Mbits/sec
[ 3] 9.0-12.0 sec 7.75 MBytes 21.7 Mbits/sec
[ 3] 12.0-15.0 sec 7.38 MBytes 20.6 Mbits/sec
[ 3] 15.0-18.0 sec 7.25 MBytes 20.3 Mbits/sec
[ 3] 18.0-21.0 sec 7.88 MBytes 22.0 Mbits/sec
[ 3] 21.0-24.0 sec 7.62 MBytes 21.3 Mbits/sec
[ 3] 24.0-27.0 sec 7.75 MBytes 21.7 Mbits/sec
[ 3] 27.0-30.0 sec 7.88 MBytes 22.0 Mbits/sec
[ 3] 0.0-30.1 sec 75.5 MBytes 21.1 Mbits/sec
Note that Norton Antivirus popped up and warned about the iperf traffic; the default recommended action was to block it.
Your AV may simply quietly block it. So if ssh and the web interface are working but not iperf; check your antivirus software. YMMV.
The video moves on to trying performance with a 5GHz band. I don't have any other 5GHz routers, so I could not test this.
Important thing to note is that he ended up apparently needed to power cycle the router when changing from 2.5GHx to 5GHz.
So on to
SDR "Sharp" (which was also already install in the video). You can
download the AirSpy SDR# here. Norton AV gave me a ton of grief on many of the SDR# executables. Here's the config in SDR#. The only thing is setting the IP address for RTL-SDR (tcp):
Although the original pic above has the RTL-SDR plugged directly into the router, it is probably a good idea to use an extension cord, as shown in the video to get the receiver a bit farther away.
Note that we are port forwarding the br-lan address: 192.168.2.1 from the 192.168.1.x network. Thus we need to tell rtl_tcp to listen on that address:
rtl_tcp -a 192.168.2.1 -f 95300000
Press play button in SDR# and voila!
Resources, Inspiration, Credits, and Other Links: